Web Security 08 - Sniff
| Published: | Thu 28 February 2019 |
| By: | Brian Shen |
| Category: | Security |
| Tags: | Security Web MIME Sniff Web Security |
All the sample code is in https://github.com/brianshen1990/WebSecurity .
1. What is MIME Type
A Multipurpose Internet Mail Extensions (MIME) type is a standard that indicates the nature and format of a document, file, or assortment of bytes.
Browsers use the MIME type, not the file extension, to determine how to process a URL, so it's important that web servers send the correct MIME type in the response's Content-Type header. If this is not correctly configured, browsers are likely to misinterpret the contents of files and sites will not work correctly, and downloaded files may be mishandled.
General Types:
- applicationList (application/octet-stream, application/pdf, application/pkcs8, and application/zip)
- audio (audio/mpeg, audio/vorbis)
- font (font/woff, font/ttf, and font/otf)
- image (image/jpeg, image/png, image/gif, and image/svg+xml)
- model (model/3mf and model/vml)
- text (text/html, text/plain, text/html, text/javascript, text/css)
- video (video/mp4)
2. What's MIME sniffing
In the absence of a MIME type, or in certain cases where browsers believe they are incorrect, browsers may perform MIME sniffing — guessing the correct MIME type by looking at the bytes of the resource.
Each browser performs MIME sniffing differently and under different circumstances. (For example, Safari will look at the file extension in the URL if the sent MIME type is unsuitable.) There are security concerns as some MIME types represent executable content. Servers can prevent MIME sniffing by sending the X-Content-Type-Options header.
3. Sample
Let's see what happened in our blog system:

Warning
If a file is cached in our browser, then we cannot see the content type in DevTools.
Let's modifying our system ( index.html ):
<script src="./userImage.txt" ></script>
userImage.txt :
alert('I take over the browser!');
And run our system:
node index.js
It seems that the txt plain file is being executed!
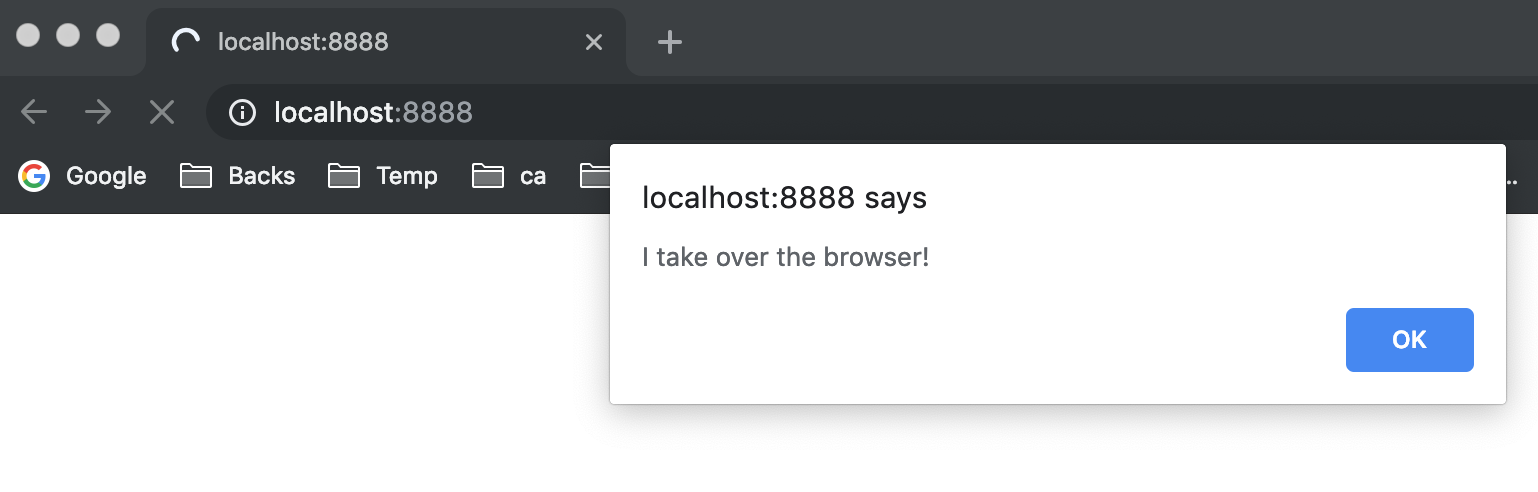
What if our system allows users to upload txt file types, and some bad guys upload a txt file full of scripts, and in the blog content, they somehow import this scripts, then XSS attack can be happened.
4. How to fix
- Stop browser performing MIME sniffing
- Send the correct MIME Type
Now let's build a safe website indexSafe.js :
// ...
app.use(helmet.noSniff());
// ...
And run our system:
node indexSafe.js
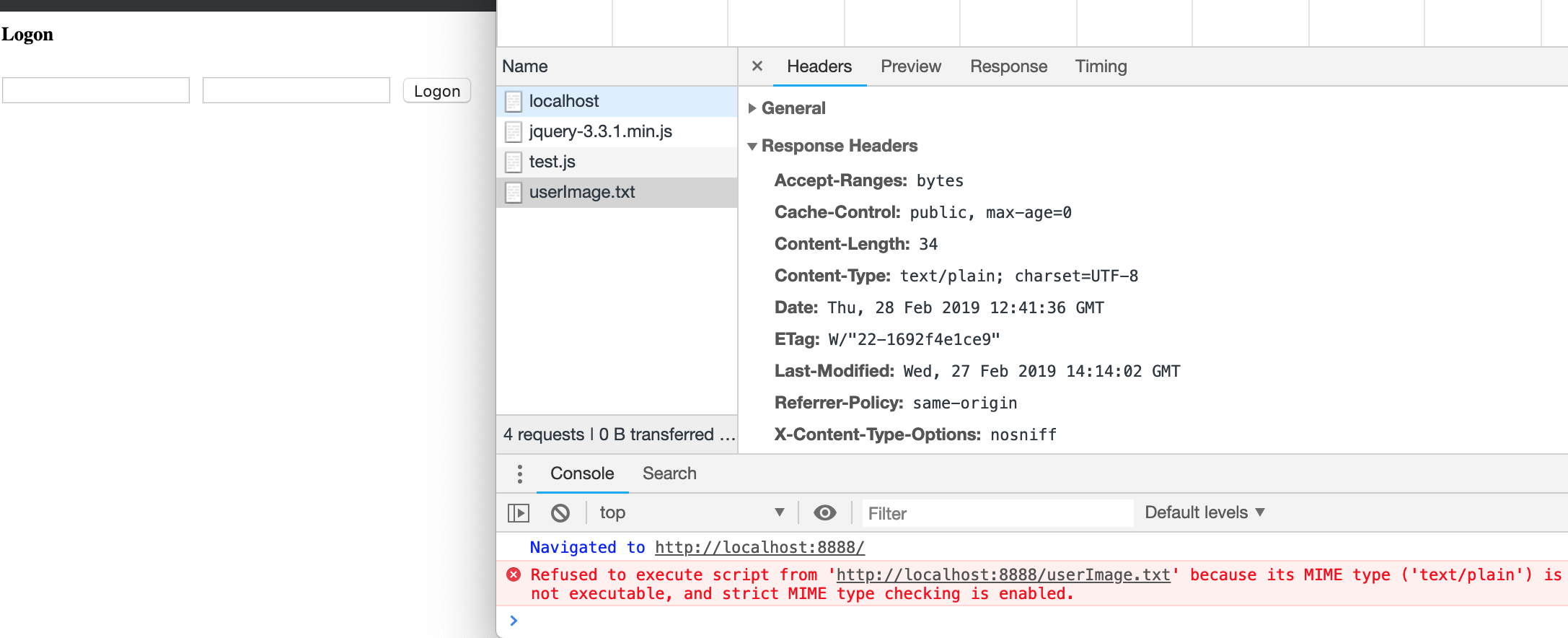
The plain txt file won't be executed any more.
https://developer.mozilla.org/en-US/docs/Web/HTTP/Basics_of_HTTP/MIME_types

Comments !